DATABRICKS TECHNOLOGY PARTNER FOR DATA SECURITY
Maximize the value of your data while preserving privacy
Comforte offers innovative data-centric security solutions to Databricks customers as an Integrated Partner Solution. This partnership allows users of the Databricks platform to securely accelerate and scale their strategic initiatives in becoming data-driven enterprises.
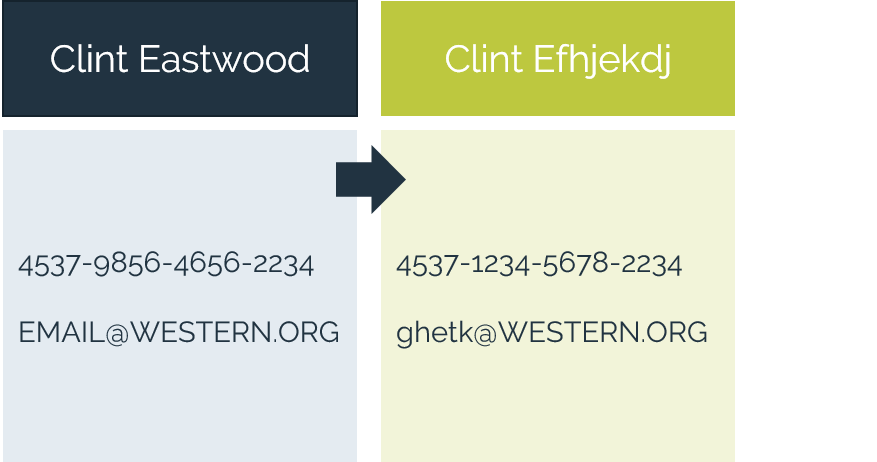
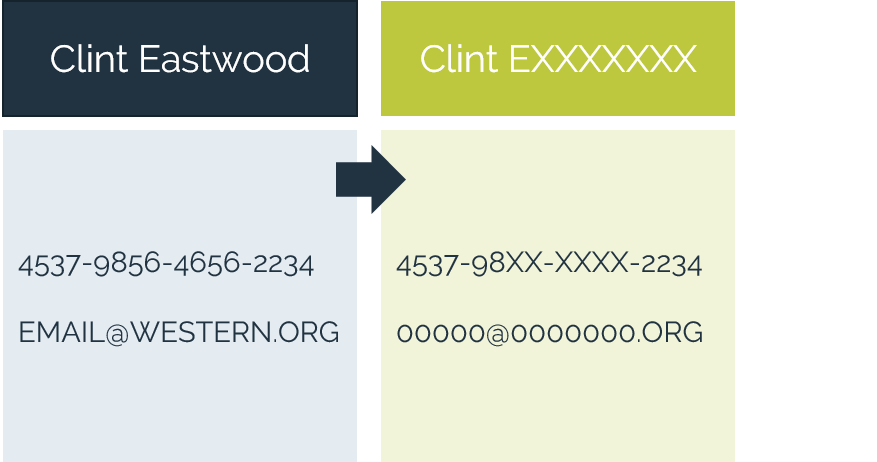
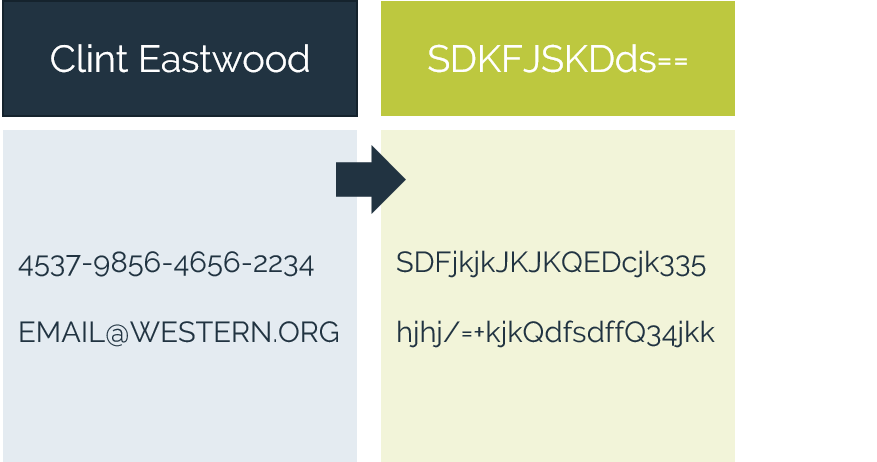
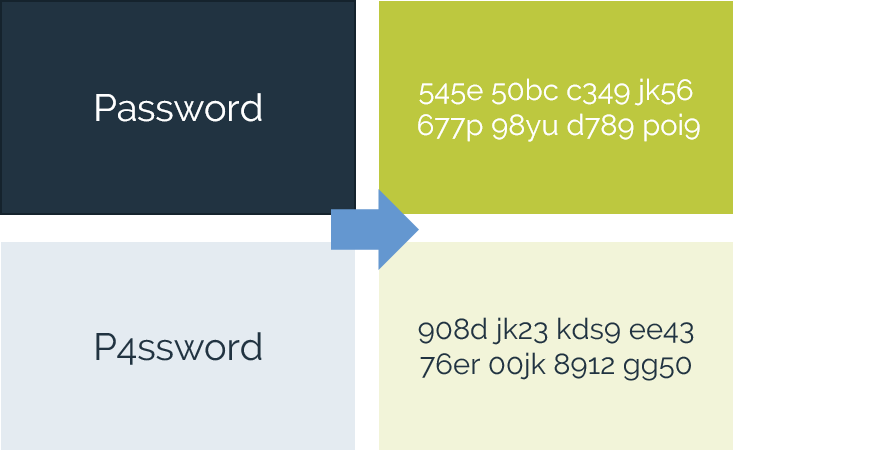
Our approach prioritizes safeguarding the data itself, employing a data-centric security strategy. This means that even in the event of a data breach, the exposed data remains indecipherable and useless to unauthorized parties. We offer simple, robust solutions for data discovery and encryption, providing a comprehensive layer of protection against data threats.

comforte Data Protection Technologies
Why work with us
- Proven industry leadership – over 25 years of experience in protecting mission-critical systems for banks, payment providers, insurers, retailers, healthcare organizations and others.
- Global trust and reliablity – secures data for more than 500 enterprise clients worldwide.
- Protect data elements from capture – keep data protected, at-rest, in-motion, in-use - in applications and analytics.
- Preserve data utility while keeping it secure – eliminate complex key management challenges.