How TAMUNIO Turns Sensitive Data Into Safe Data
Discover what’s sensitive, apply the right controls, and enable governed access so data stays protected, audit-ready, and ready for analytics and AI.
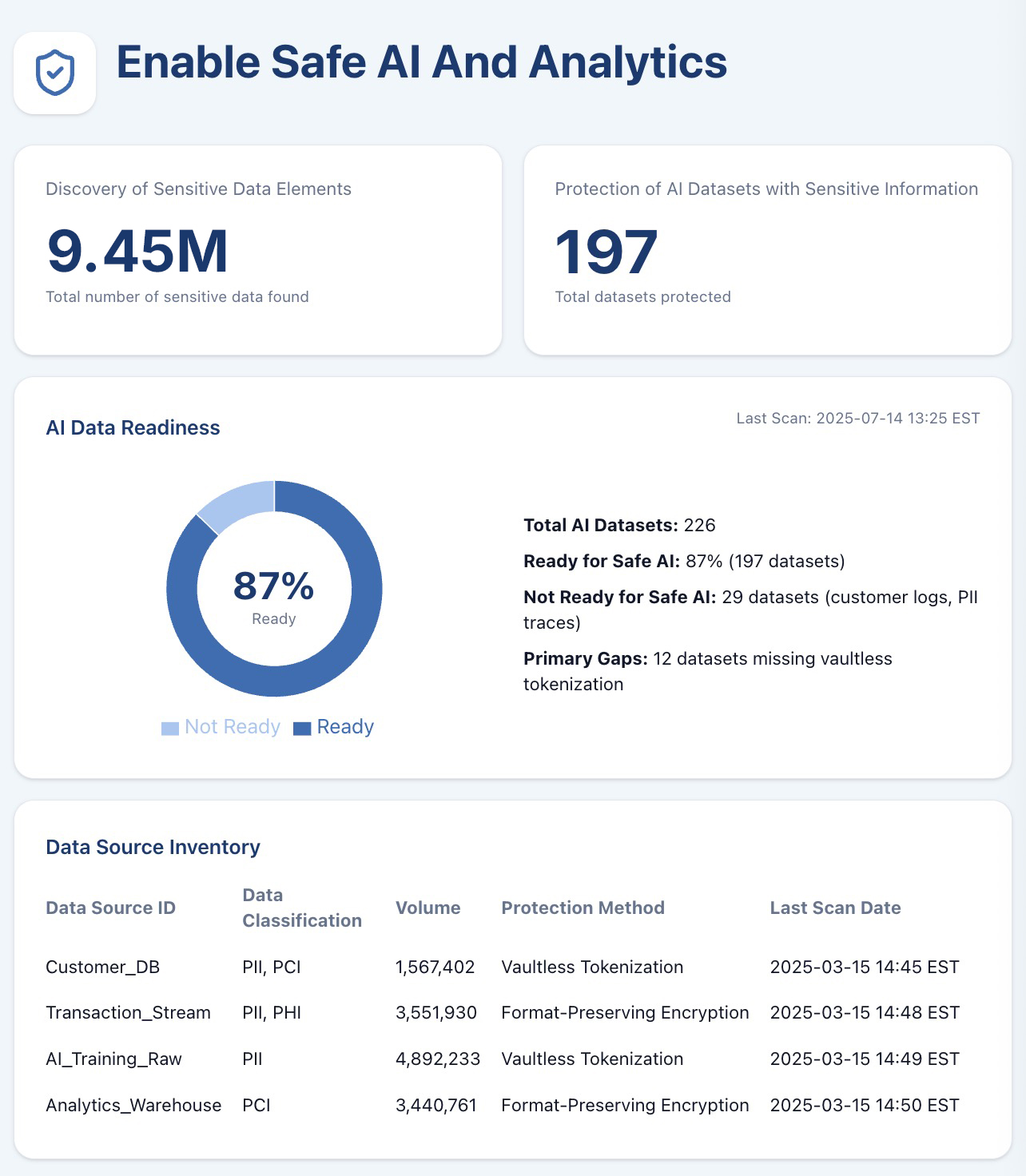
See the platform in actionTAMUNIO | End-to-End Journey
1. Discover & Classify
- Scan across enterprise data environments
- Identify sensitive and business-critical information
- Use AI-assisted detection for free text and unstructured sources
-> Visibility without manual inventories
2. Protect
- Apply field- and file-level controls that travel with data
- Enforce centrally defined policies at scale
- Keep data useful for analytics and AI with format-preserving methods
-> Stolen data is unreadable; analytics and apps keep working
3. Govern & Monitor
- Manage policy, keys, access, and approvals in one place
- Stream events into SIEM/SOAR for monitoring
- Generate audit-ready evidence on demand
-> Faster audits, smaller scope, quicker incident response
"Both the solution, as well as the services provided by comforte‘s specialists were fundamental to deliver a successful project. Comforte’s experience in implementations of this kind was noticed at all times, and also their ability to cater for the specific needs that clients like us usually have trying to comply with PCI DSS regulations."
Humberto Padilla Loza, Production and Support Director at City Fresko Hypermarkets
Why TAMUNIO is Different
| The Old Way | With TAMUNIO |
|---|---|
| Perimeter controls only | ✔ Data-level protection that travels with the data |
| Rigid, stateful systems | ✔ Stateless, scalable services that adapt to demand |
| Costly, complex integrations | ✔ API-first and cloud native approach |
| Disconnected audit trails | ✔Centralized monitoring and reporting |
| Cloud and AI blocked by security and privacy concerns | ✔Data Sovereignty Zones keep data protected in use and fully under customer control even in the public cloud |
TAMUNIO Architecture at a Glance
Overview
TAMUNIO is designed for operational simplicity at a global scale. It supports on-premises, hybrid, and cloud-native environments and is organized into three layers.
It is composed of three primary layers:
| Core Layer | Purpose | Key Components |
| Management Layer | Control and visibility | Management Console, Audit Console, Observability Platform |
| Protection Layer | Applies policy and protection | Structured/unstructured protection services, PII detection, Data Sovereignty Zones with Confidential Computing |
| Integration Layer | Connects to your stack | APIs/SDKs, proxies, virtual file system, adapters, connectors |
Management Layer
Govern once, apply everywhere
TAMUNIO’s control hub is the single source of truth for policies, keys, approvals, and audit evidence. It brings the Management Console, Audit Console, and Observability Platform into one layer, so protection stays consistent, controlled, and verifiable.
- Central policy and access control
- Audit-ready evidence and reporting
- Operational visibility with SIEM integration
Protection Layer
Apply policy, protect data
A stateless, vaultless* services layer that enforces controls across structured, unstructured, and free-text content while preserving utility for analytics and AI.
- Broad coverage across databases, files, documents, logs, and streams
- Controls include vaultless tokenization, format-preserving encryption, masking, and file encryption
- Confidential Computing to minimize plaintext exposure during processing
- AI-assisted detection for PII in unstructured content
- Analytics-ready modes that preserve data relationships
- Options for post-quantum readiness and Data Sovereignty Zones
(* Stateless: no user session state. Vaultless: no centralized sensitive-data store.)
Integration Layer
Sclable, Flexible Deployment
Connect protection services to your existing systems, applications, and pipelines without major rewrites.
- APIs & SDKs to embed protection into apps and SaaS workflows
- Transparent integration using proxies/adapters where code changes are not practical
- Virtual File System and connectors for cloud services, data stores, messaging, and middleware
Protect Data Wherever It Flows
Wherever sensitive data moves (across cloud, on-prem, analytics, or AI pipelines), TAMUNIO integrates directly into your systems to keep it secure.
| Where Your Data Lives | Integration Approach | Typical Use Case |
|---|---|---|
| Databases & Data Stores | Policy-driven integration | Protect payment card numbers or customer IDs without schema breakage. |
| Vector Databases | Field-level protection | Protect sensitive data for RAG and GenAI by de-identifying before indexing and ensuring safe use at query time. |
| Files & Reports | File-level protection | Encrypt PDFs, images and exports. |
| Streams & Pipelines | Data-in-motion controls | De-identify data before analytics or lake ingestion. |
| System Workflows | Workflow protection | Apply tokenization or FPE as customer records move into a data warehouse or lake. |
| APIs & Apps | APIs and SDKs | Embed protection in payments flows, web and mobile apps or AI training pipelines. |
Major US Insurer Meets NACHA Requirements and Unlocks Safe Analytics
This insurer achieved NACHA compliance while enabling safe analytics and fraud detection.
- Secured PII and payment data across AWS and BigQuery
- Enabled governed analytics using de-identified datasets
- Reduced audit effort with continuous discovery and reporting

FAQ
How do you detect sensitive data in free text?
AI-assisted detection finds personally identifiable information (PII) and regulated fields in documents and logs, feeding classification and policy decisions.
What is a Data Sovereignty Zone?
A Data Sovereignty Zone is a secure, isolated cloud environment built on confidential computing that keeps sensitive data protected even during processing. It ensures that plaintext data only exists inside trusted enclaves under customer control, enabling highly secure use cases like private AI or analytics.
Can authorized users still see the original values?
Yes, via policy-controlled de-protection with approvals and logging.
How do analytics and Machine Learning remain accurate?
Format-preserving methods and relationship-aware protection ensure models and reports work without revealing raw values.
What’s the typical first project?
Most organizations start with a high-value flow such as cardholder or customer data in an analytics or payment pipeline, then expand by connector or domain.