TAMUNIO: One Platform to Secure Enterprise Data Everywhere
Bringing together discovery, policy enforcement, and protection for confident data use in analytics and AI across platforms.
Explore TAMUNIO capabilitiesWhy TAMUNIO is the Future of Enterprise Data Security
Comforte has a strong track record of helping organizations safeguard mission-critical systems and sensitive information at scale. Building on this foundation, TAMUNIO addresses today’s enterprise challenges in security, compliance, and innovation.
TAMUNIO secures structured and unstructured data with AI-driven detection and Confidential-Computing–based Data Sovereignty Zones, backed by a unified governance layer for consistent controls across environments.
The result is reduced impact from data breaches, simplified compliance, and the confidence to safely leverage protected data for analytics, AI, and modernization initiatives.

Why comforte
3 Steps to Safer Data
1. Discover & Classify
AI-powered data discovery finds and labels sensitive data across databases, data lakes, files, logs, streams, SaaS, and AI pipelines.
-> Know exactly what to protect and where to act.
2. Protect
Apply data-centric controls at the field and file levels that stay with your data across environments. Use Data Sovereignty Zones with Confidential Computing when plaintext is required.
-> Stolen data stays unreadable while apps and analytics keep working.
3. Govern & Monitor
Manage policies, keys, access, and approvals in one place; stream events to SIEM/SOAR; produce audit-ready evidence on demand.
-> Simpler compliance proof and faster incident response.
"Mercury is dedicated to staying ahead of the game and so we have added another layer of defence to protect our customers’ data. This will offer us even greater support in our mission to deliver reliable services safely and securely."
Jasna Fumagalli, Compliance, Security and Risk Management Director at MPSI (now Nets part of the Nexi Group)
TAMUNIO Platform Highlights
| Key Features | Challenge TAMUNIO Solves | Business Impact |
|---|---|---|
| AI-Powered Discovery | Sensitive data scattered across systems | Detect and protect data types across your system landscape. → Reduces blind spots and breach risk. |
| Data-Centric Security Approach | Traditional protection methods make data unusable | Replace sensitive fields with secure, format-preserving values. → Minimizes risk without disrupting processes and applications. |
| File-Level Encryption | Unstructured data exposure | Consistent protection across collaboration tools and file workflows. → Secures high-risk reports, documents, and exports. |
| Data Sovereignty Zones (Confidential Computing) | Compliance blocks cloud processing | Keep sensitive data secure in use and under customer control, even in shared or public cloud environments. → Enforces data sovereignty without blocking analytics or AI. |
| Quantum-Ready Protection | Long-lived data faces future cryptographic risk | Enable quantum-safe protection for data at rest and in motion. → Provides future-ready protection. |
| Unified Management & Observability | Disparate tools slow audits | Centralize policies, keys, and SIEM integration. → Enables faster audits and response. |
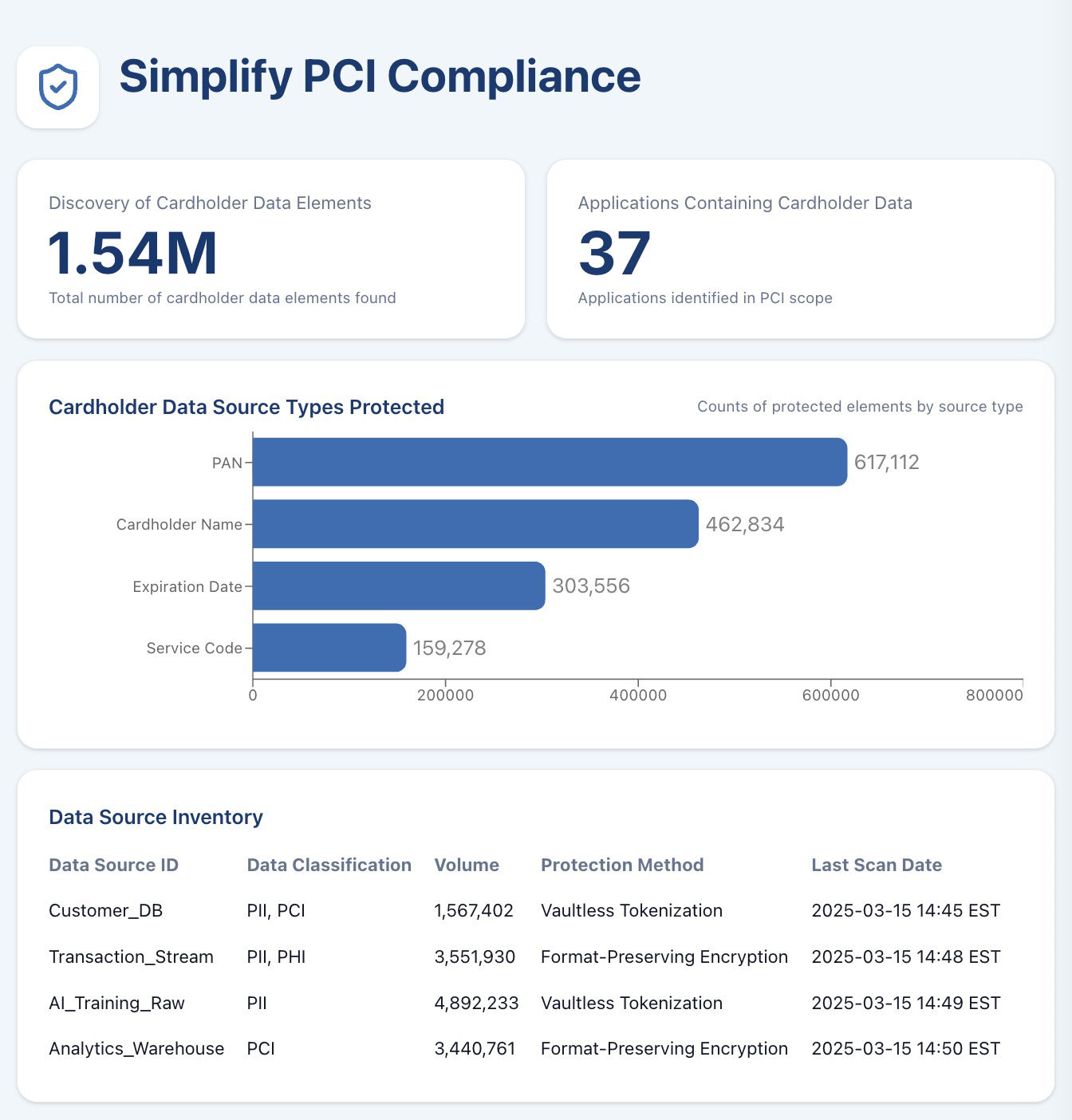
How a Leading Indian Bank Cut PCI Scope and Enabled Safe Analytics
Data-centric security at enterprise scale for 100M+ customers.
- Secured cardholder data against attacks
- Enabled governed analytics using de-identified datasets
- Reduced PCI DSS scope and audit effort

One Platform for Teams, Compliance, and Every Environment
Compliance Coverage
| Regulatory Framework | How TAMUNIO Helps | Status |
| PCI DSS 4.0 | Assists with requirements by protecting primary account numbers (PAN) and related data, produces signed audit trails and access logs. | ✅ |
| GDPR | Supports minimization and de-identification, plus auditable access logs. | ✅ |
| DORA | Centralizes policy, logging, and SIEM integration to provide evidence for ICT risk management and incident reporting. | ✅ |
| NIS2 | Automates discovery and classification, enforces access control, and supplies audit trails to support security monitoring and incident response. | ✅ |
For Security, Privacy, and Data Teams
TAMUNIO meets each team where they work and delivers a consistent layer of control across the organization.
| Team | How TAMUNIO Helps |
| Security & SecOps | Data-level controls reduce breach impact; centralized policy and fine-grained access improve response. |
| Operations & Core Systems | Secure mission-critical workloads with low latency. Centralize key and secret management. Maintain uptime and performance. |
| Privacy, Risk & Compliance | Automate discovery, apply consistent controls, and streamline gathering assessment evidence across frameworks. |
| Data & Analytics Teams | Use de-identified, format-preserving data that keeps referential integrity, so analytics and AI deliver value without exposing raw personally identifiable information (PII). |
| DevOps & Engineering | Integrate protection via APIs, SDKs, and connectors without major code rewrites. |
| Product & App Teams | Build and release features using data that looks and works like real data, but with sensitive details hidden and unreadable if leaked. This way, they can develop safely without exposing private information. |
Where TAMUNIO Protects Your Data
| Environment | Typical Workloads | How TAMUNIO Fits In |
| Public or Hybrid Cloud | Apps, storage, databases, servers, data platforms | Deploys alongside your existing services in the cloud or on-premises. |
| Core Business Systems | Mission critical systems for payments and operations | Adds a strong protection layer without application rewrites. |
| Databases & Warehouses | Customer, payment, or transaction data | Integrates through pre-built connectors and format-preserving protection. |
| Streaming Data & Lakes | Event streams, real-time logs, ingest pipelines | Protects data as it’s collected or moved downstream. |
| Files & Documents | Shared folders, reports, exported data, internal documents | Applies file encryption and policy to protect documents and shares. |
| AI & Analytics Pipelines | Training datasets, dashboards, and LLMs | Provides de-identified data that preserves utility. |
FAQ
Is TAMUNIO built on proven technology?
Yes, it builds on comforte's trusted data security platform, already securing billions of transactions daily.
Will protection break schemas or downstream tools?
No, format-preserving methods keep data shape and relationships, so warehouses and data pipelines can continue to operate.
What integration options are available?
TAMUNIO integrates flexibly through APIs, SDKs, connectors, and transparent deployment options designed to fit into existing applications and data flows without major rewrites.
We’re a HPE Nonstop customer, how does this fit?
TAMUNIO unifies HPE Nonstop with enterprise/cloud protections and governance into a single platform.
How do I get started?
Contact our team: https://www.comforte.com/contact
or schedule a demo: https://www.comforte.com/request-demo.