Protect sensitive data across Temenos Transact workflows
A joint ITSS and comforte solution powered by TAMUNIO
Book a demoStop Security Concerns from Slowing Your Transact Modernization
Every time data leaves Temenos Transact for operations, reporting, analytics, and AI, the exposure surface can grow. Readable sensitive information and payment data can spread into interfaces, exports, and environments. That increases compliance effort, raises incident impact, and slows modernization, AI and cloud programs.
The better approach is to protect sensitive fields early, keep them protected as they move through connected systems, and restore readable values only where required under explicit policy and audit.
Read the Fact Sheet
TAMUNIO Connector for Temenos Transact
Trusted Data Protection for Temenos Transact: ITSS + comforte
The TAMUNIO Connector integrates with Transact using Temenos-aligned extension points. It protects high-risk PII and payment-related fields using tokenization. Protected values can be used across connected systems by default, with readable data restored only at approved outputs.
Book a demo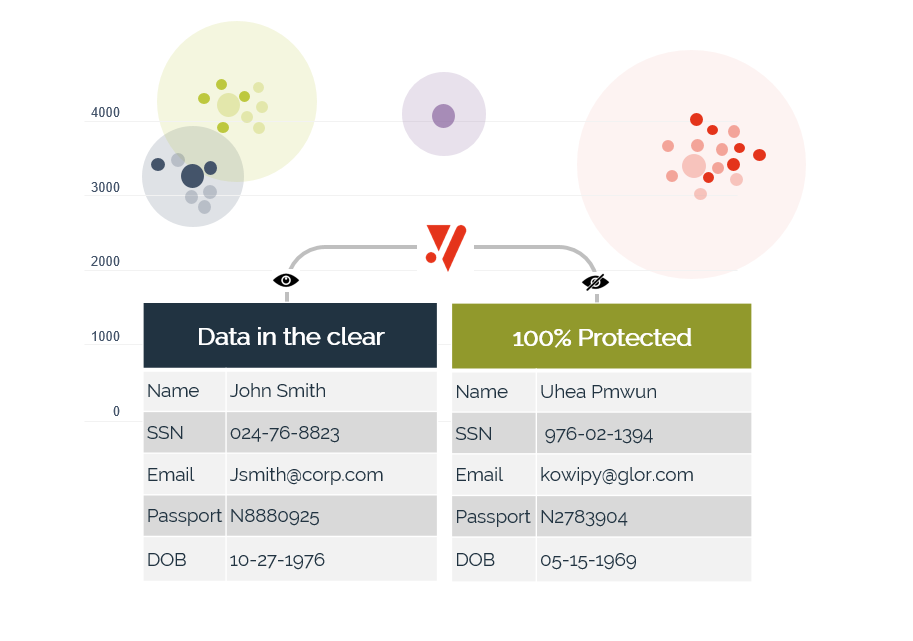
How it Works
1. Inbound Protection
Tokenize defined sensitive fields in supported Transact flows.
2. Secure Processing
Use protected values across connected workflows and downstream systems.
3. Outbound Controlled Reveal
Restore readable values only for approved use cases, users, and outputs.
Secure Your Transact Workflows Without the Complexity
A Structured, Low-Risk Deployment.
Discover
Map key data flows and identify priority fields and outputs.
Design
Set policies, roles, and approved reveal points.
Integrate
Deploy using Temenos-aligned integration points.
Validate
Test end-to-end flows and confirm controls and evidence.
Why Choose the Transact Connector for Data Protection?
ITSS + comforte: Two Leaders. One Integrated Solution
Combining deep Temenos delivery expertise with data-centric security powered by TAMUNIO. Together, we bring ITSS’s 23+ years of Temenos implementation experience and comforte’s 25+ years of data-centric security expertise.
- ITSS: 850+ consultants supporting core banking transformation and cloud programs.
- comforte: Data-centric security expertise to help protect high-risk financial data across connected environments.

FAQ
What is the TAMUNIO Connector for Temenos Transact, and what does it do?
An ITSS-delivered integration powered by comforte TAMUNIO that helps protect defined sensitive fields in Transact workflows using tokenization.
What data types can it protect?
Defined PII, customer and account identifiers, and payment-related fields, scoped to your requirements.
Where in the Transact environment is protection applied?
Across supported Transact workflows and integration points identified during discovery and implemented in phases.
How does controlled reveal work, and who can access readable values?
Readable values are restored only at approved reveal points for authorized roles or systems under policy and audit.
How does this support banking regulations and audit expectations?
It helps reduce where readable sensitive data exists and strengthens control and evidence across connected environments to support regulatory and audit requirements.
Enhance data security and move faster with Transact.
Book a Temenos Transact data protection demo.
See how data-centric protection can enhance security, streamline compliance and support modernization and data-driven programs.
