comforte Data Protection
DownloadProtect all your sensitive data
All companies retain highly sensitive information about their own employees, intellectual property, and business strategies, but many of them also collect, handle, process, and store highly sensitive information about prospects and customers. This data includes personally identifiable information (PII), payment details, and depending on the industry even health and personal records.
All of this information requires very careful handling and processing, mostly by regulatory mandate but also by the ethics of good business. Keeping customer data safe ultimately means building and maintaining their trust in your organization. How you decide to protect it cuts to the core of your ongoing reputation with your customers.

Digital Innovation and Hyper-agility
The enterprise that fully embraces digital innovation gains a distinct competitive advantage.
Trends like digital commerce, digital transformation, and SaaS & cloud services are significant, but they are just milestones in the march to achieve real digital innovation as an aspect of the company’s operational strategy. Digital innovation is multi-dimensional: at the intersection of strategy, technology, process, and invention.
As such, digital innovation as an enabler of business is incredibly powerful—but when the organization makes shortcuts and sacrifices with data protection in order to drive the digital innovation engine, security or compliance become imposing roadblocks.

68% of industry influencers cited data security as the biggest challenge in moving to the public cloud
What you need to know
Pay attention to Integration Demands
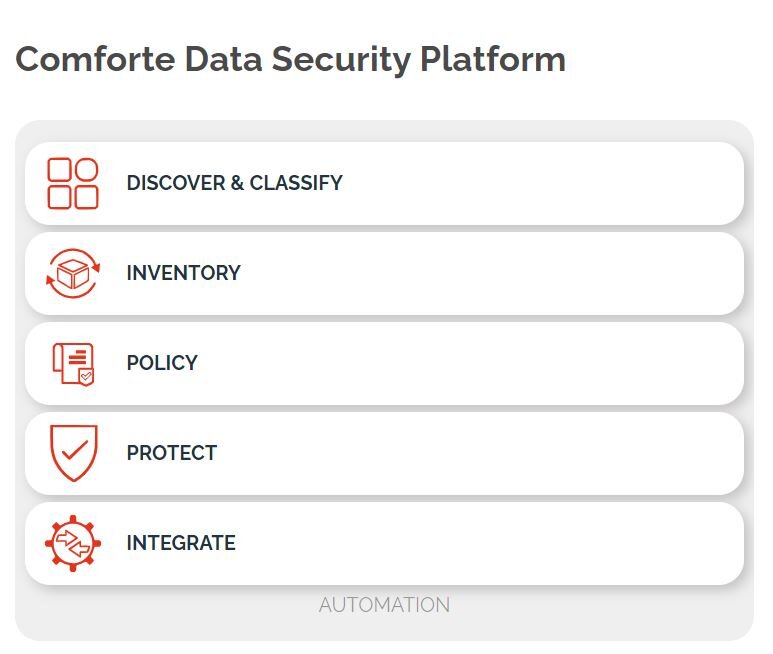
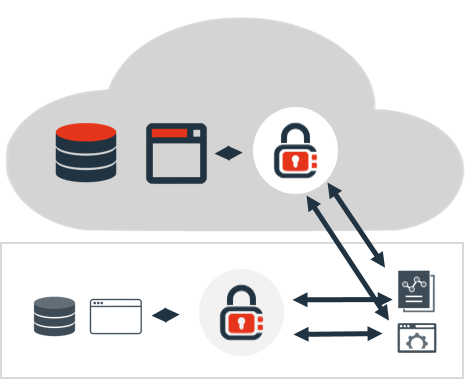
The protection system that handles the conversion from live to protected data enables granular control, visibility, audit, and reporting over all sensitive data access. For policy management and enforcement, companies can leverage standard Identity and Access Management (IAM) infrastructure. The platform also creates a solid audit trail and allows stakeholders to gain real-time insights around data protection in the enterprise.
Our entire solution reduces implementation costs and effort to a minimum in order to shorten project time and avoid service interruptions. The basis for our platform is the flexible and sophisticated integration framework, which allows multiple layers of data protection for new and existing applications.
Comforte’s data security platform seamlessly integrates with other enterprise data protection solutions and provides a comprehensive and mature set of capabilities that enable data-related risk reduction. The result is a reduced time to success with a more streamlined transition.
For IT security & operations teams
For line of business and risk & compliance teams
Our data security platform has been built from the ground up to best address data security in a world that is driven by digital business innovations, empowered customers, and continuous technology disruptions. Today it is protecting hundreds of millions of payment transactions, healthcare records, insurance records, and other personally identifiable information (PII), reliably running in business-critical environments.
At comforte, we understand the importance and value of data protection. For 20 years, we have helped leading organizations worldwide to protect their most mission-critical assets, and we have built long-term customer relationships based on professionalism and trust.